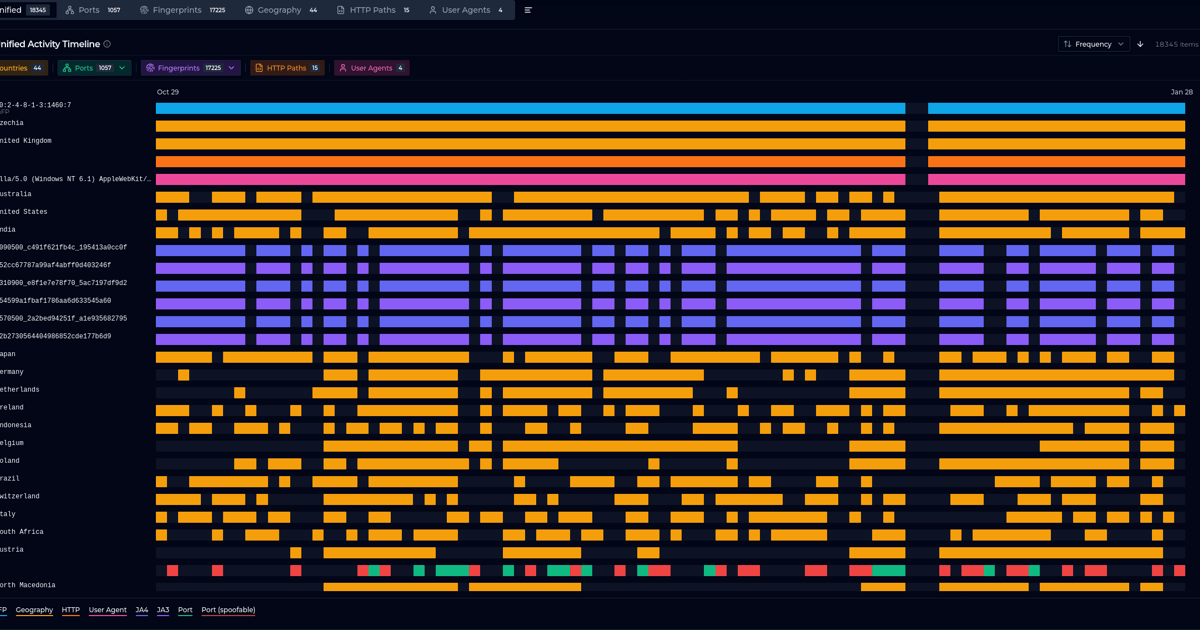
Unveiling the New Historical IP Timeline
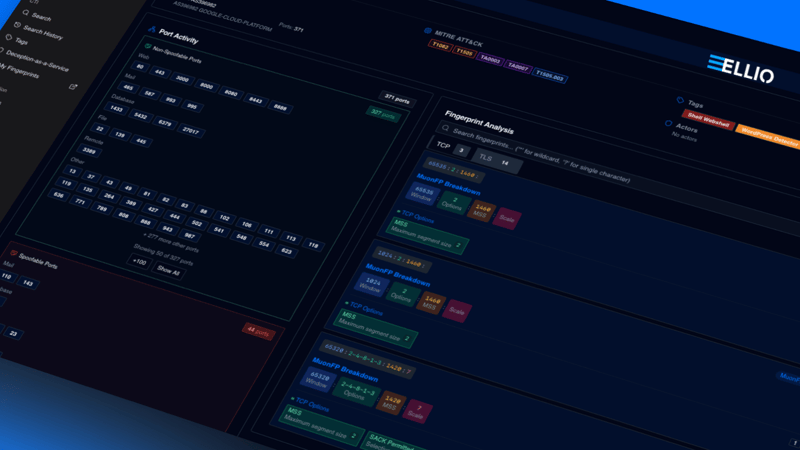
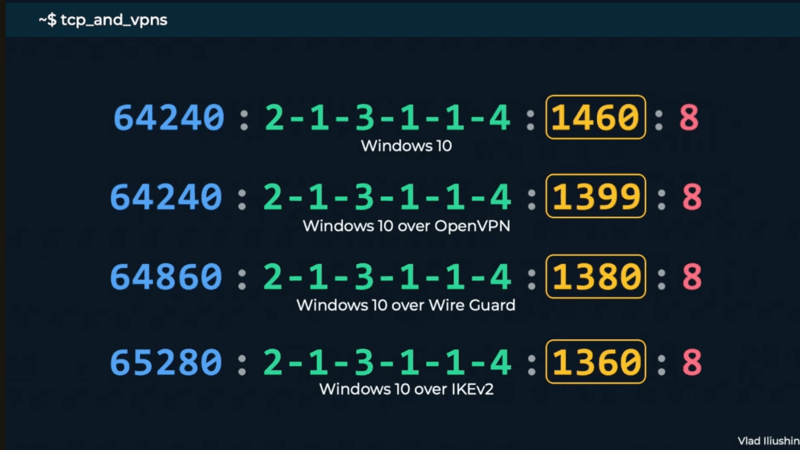
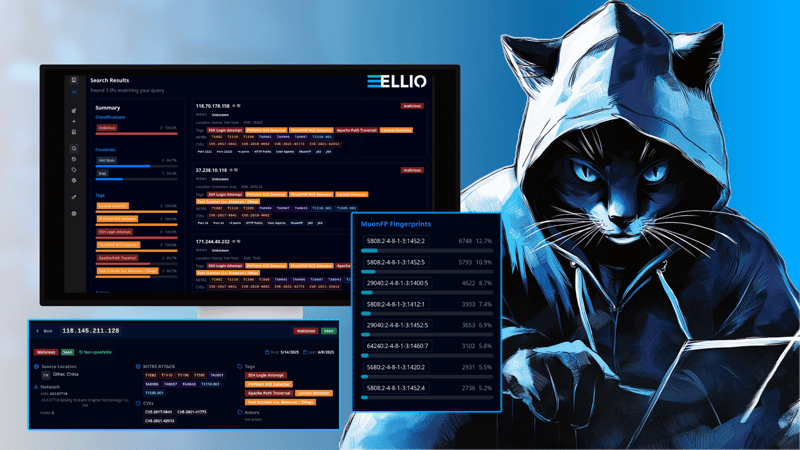
ELLIO Threat Intelligence Platform expands its capabilities with an interactive Historical IP Timeline, giving teams deep visibility into historical IP activity with flexible filtering and report-ready exports.