Network Fingerprints
Technical Articles__2 min
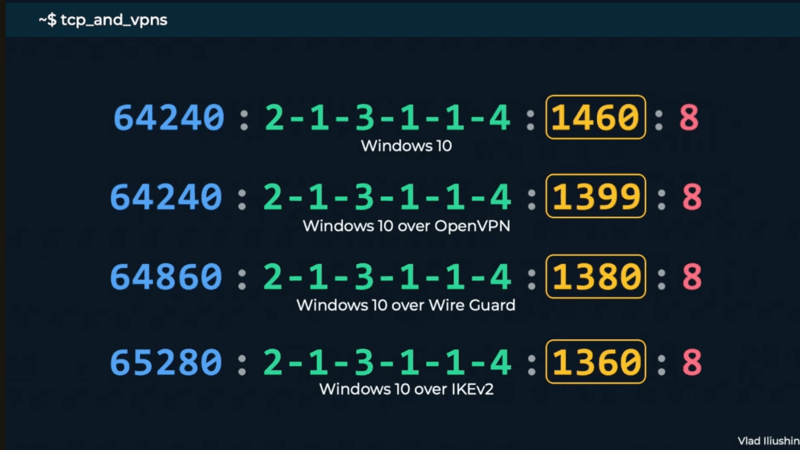
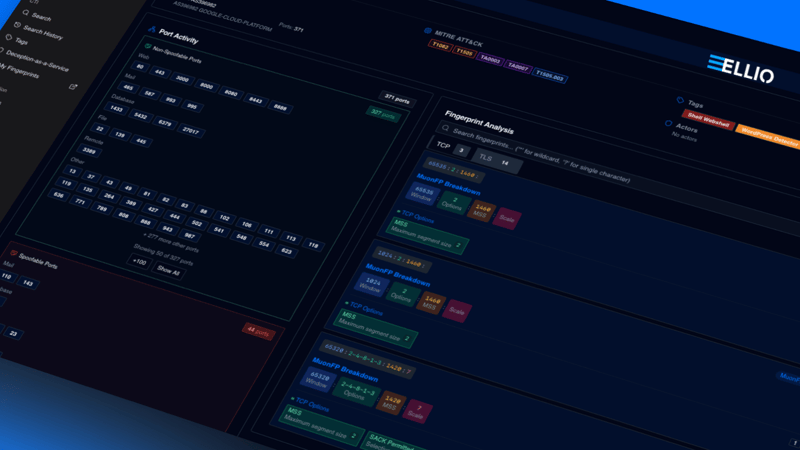
Every packet tells a story: The evolution of fingerprinting and netsec.
The journey began in 1969, when the very first RFC- Request for Comments - was published. Explore key milestones that shaped network security and the practice of network fingerprinting.