Video: How to capture real value from network fingerprinting in practice
Learn practical tips for deploying JA4, JA3, and MuonFP fingerprints in your security operations. Get expert insights from Vlad Iliushin and discover how to unlock their full defensive value.
Whether you’re focused on threat detection, blue teaming, or deeply engaged in network traffic analysis, this talk is a must-watch. At BSides San Francisco 2025, Vlad Iliushin, CEO of ELLIO and author of ELLIO Threat Platform, delivered an in-depth walkthrough of network fingerprinting and how to unlock their full value in practice.
Watch the full video and learn practical tips for deploying JA4, JA3, and MuonFP fingerprints in your security operations. Whether you’re focused on threat hunting, detection engineering, or SOC operations, this talk offers valuable insights you won’t want to miss.
In this video, you’ll learn:
- TCP/IP Fingerprinting(p0f, MuonFP)
- TLS / Layer 7 Fingerprinting(JA3, JA3S, JA3n, HASSH, JA4, JA4+)
- Differences between JA3, JA4, and MuonFP
- JA4 vs. JA4+
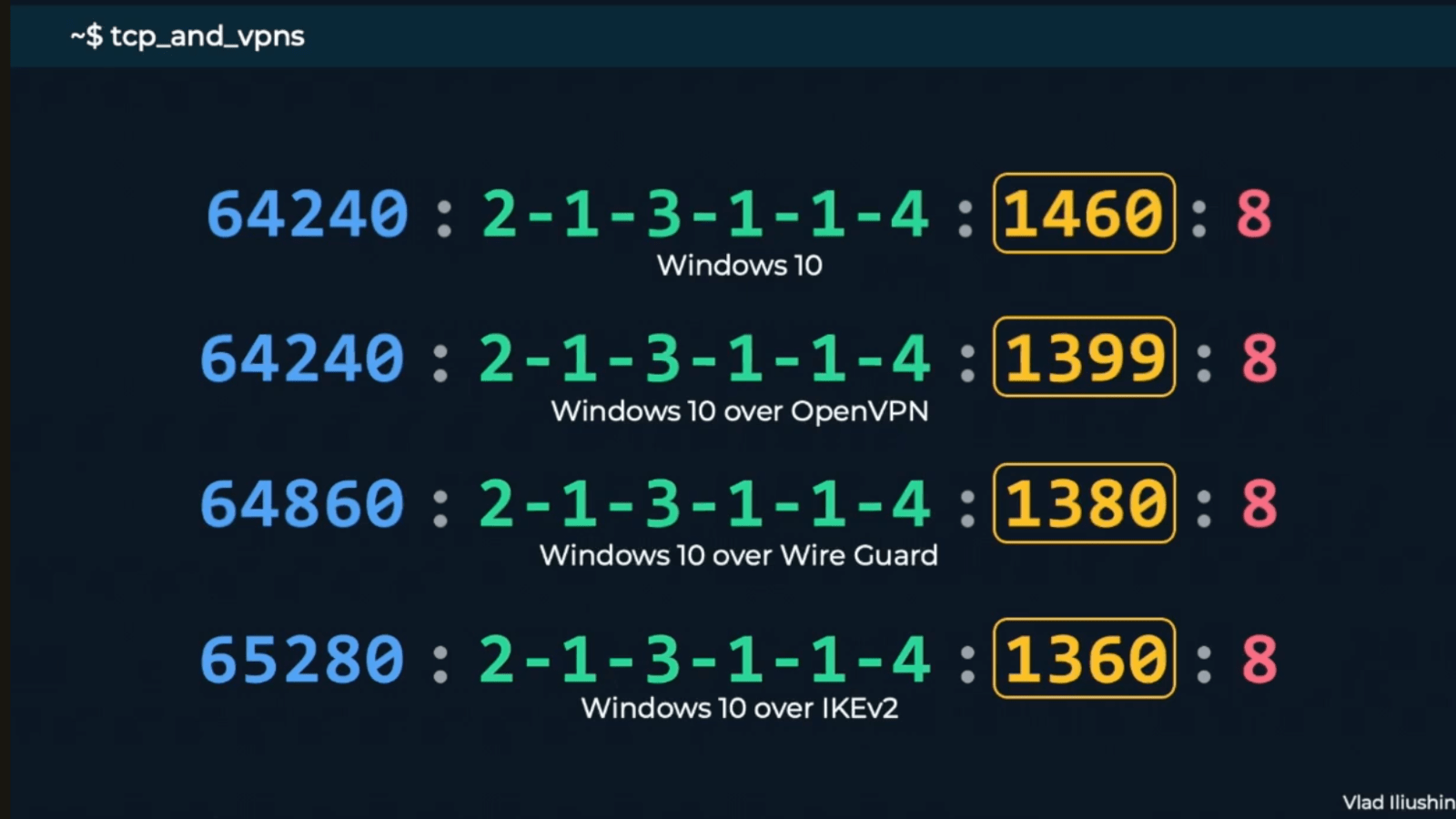
- TCP and VPNs
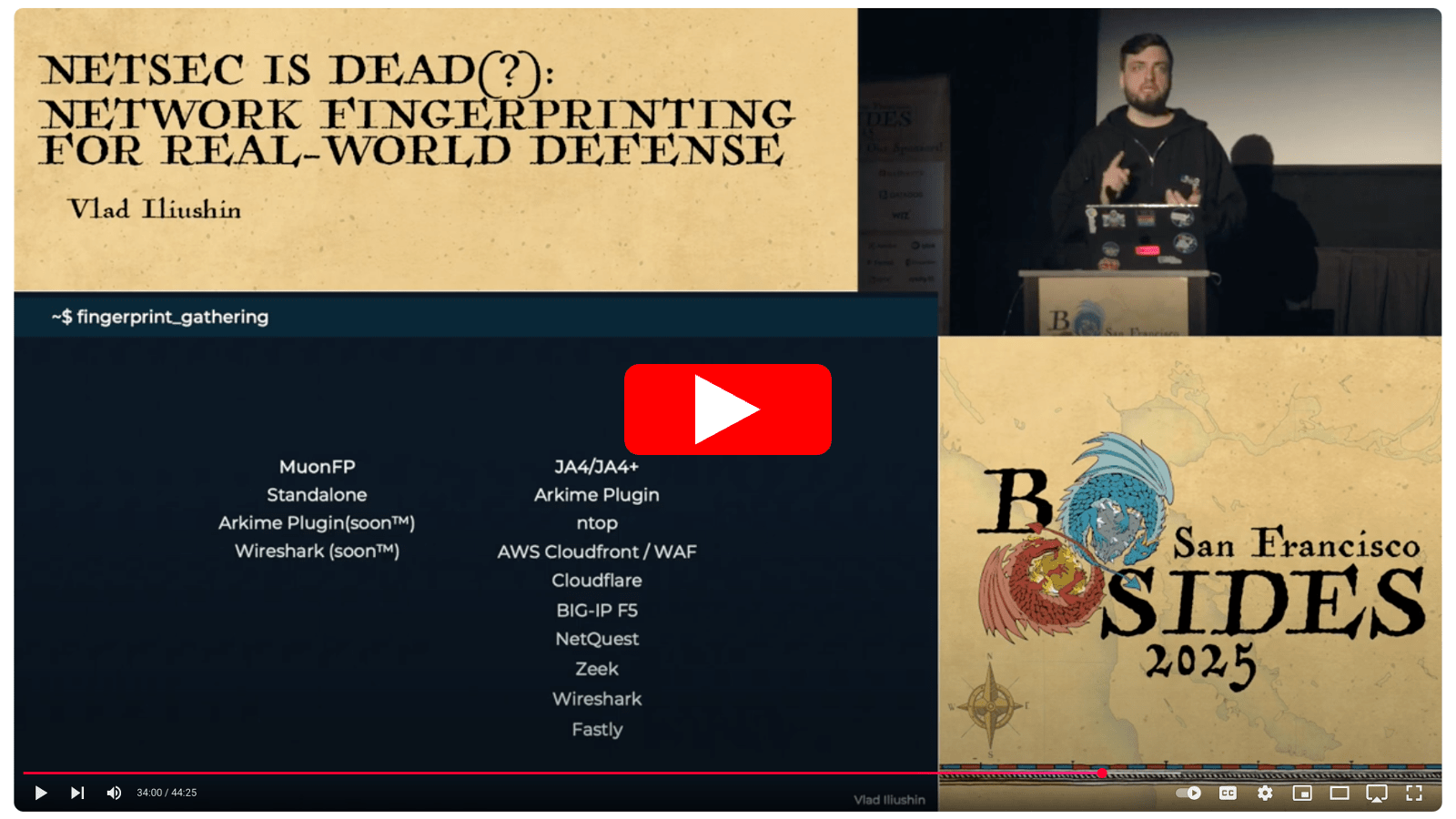
- How to Gather Fingerprints
- True value and limitations of network fingerprinting
- Fingerprint worksflows
And one fun post-show fact: with 156 slides, Vlad’s session was the largest presentation at BSides San Francisco 2025!
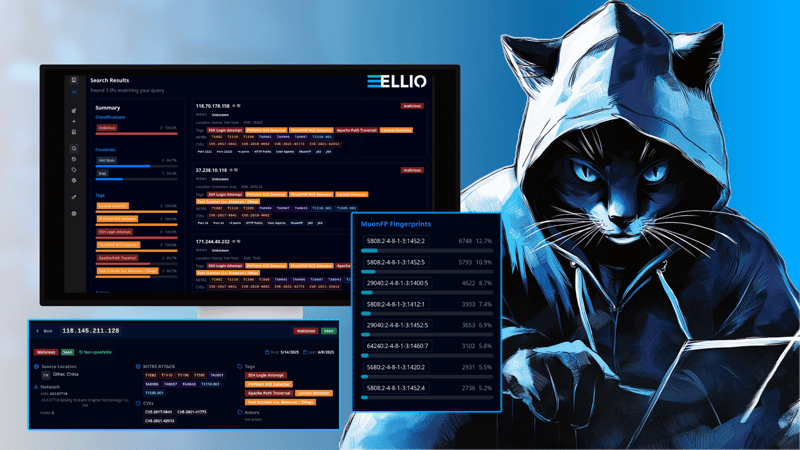
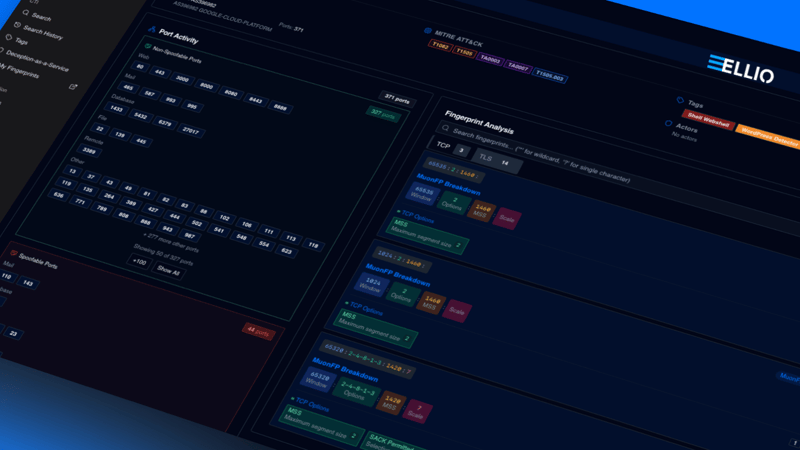
Ready to see network fingerprints in action?
Access the ELLIO Threat Platform and create your own custom threat searches using fingerprints. Discover how it can meet your specific use cases and needs.